HAVATAR - The rising cyber threat
Blog post description.
HAVATAR – The rising cyber threat
Avatar is frequently used today in automating processes and developing the metaverse field, and it is not a new term. Quoting Meriam-Webster, “Avatar derives from a Sanskrit word meaning “descent,” and when it first appeared in English in the late 18th century, it referred to the descent of a deity to the earth—typically, the incarnation in earthly form of Vishnu or another Hindu deity.”
The current definition of Avatar, based again on Merriam-Webster’s dictionary, is “an electronic image that represents and may be manipulated by a computer user (as in a game).
So, what is the problem? We, human beings, are served by virtual electronic entities – amazing.
The virtual and physical entity
Before touching on the meaning of the term HAVATAR, let’s discuss some aspects and processes leading to the rising threats and concerns.
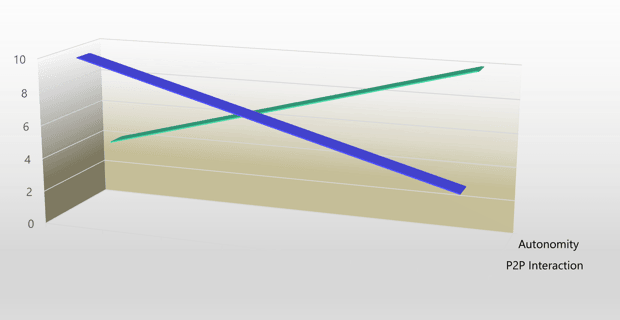
The accelerating factors of virtual entity usage are two processes – Autonomy and Person-to-Person Interaction (P2PI). The autonomy trend is soaring up, and the P2PI direction dives down. Our machines, systems, processes, and services are increasingly autonomous and unattended, and our human interactions, even the social ones, are less and less physical.
Another interesting process is a close-up of the physical and the virtual entity. To express it simply, in the same “body,” there are both entities – I call this quality “Virsicality.”

The current situation is that the most “Virsical” entity is us, human beings. Digital virtual entities can have strong virtual characteristics, but their physical ones are imperfect.
Categorizing those virtual entities, Avatars, into the interaction level (not androids or robots), we are familiar with three groups – text avatars, voice/sound avatars, and visual avatars. I am using the term Avatar, but we also call them by names like answering machines (~1940), bots, and more.
The gap is closing
The fantastic abilities brought by modern computers and AI techniques and expected to develop more by quantum technology are rapidly improving the virtual and, more concerning, the physical skills of the avatars.
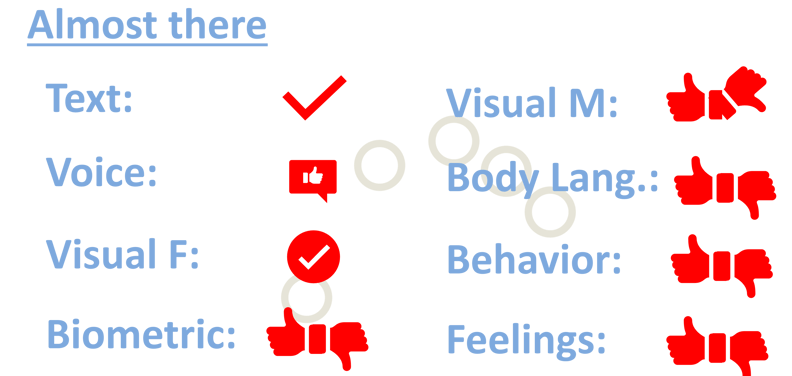
Referring to the categorization I mentioned, the text and sound avatars are almost perfect. It is tough to recognize if you are chatting or talking to a human being or an electronic entity. This situation was and is used by many cyber adversaries for various cyber attacks, false identity creation, etc. The closing gap touches the visuals, some physical aspects, and some parts of human being virtuality. To be more precise, visuals by the meaning of visual representation of the person. There are unique visualizations of human avatars based on supergraphics or even on an actual photo of a human. The term used for them is “HUMATAR” – a human-like Avatar. However, movement animation, body language, and expression are immediately recognized as artificial. Biometrics is still challenging to imitate. Human being virtuality by means of behavior, feelings, and intuition.
The challenge
The gaps will close at the end, and the virtual entities will be very real, very human. It will open new opportunities almost in any life process. On the other hand, it will open to cyber adversaries a new and highly dangerous ability to appear as someone else with all the meanings.
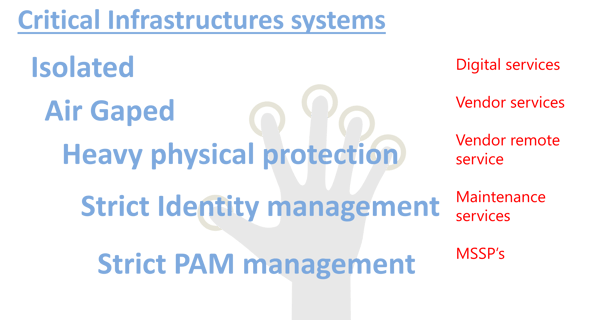
It is not touching only the IT service, and it is even more critical in the ICS/OT environment. Yes, the ICS/OT environment is much more isolated and restricted, but – digitalization, cloud usage penetration, and external services trends are excellent candidates for the Human Avatar – the “HAVATAR” cyber adversary tool.
It is not science fiction
Maybe, many of you assume that HAVATARS is science fiction. Definitely NO. We are not there yet, but close to it and moving fast. We are already witnessing and experiencing cyber attacks based on identity theft, voice and text fraud, sensitive information, and data repository access via virtual entity imitation.
We must not wait until the HAVATAR technology is mature and act immediately. The first steps organizations and regulators should take are the following:
Identity zero-trust based on enriched identification characteristics – “Initial Identification.”
Agreement-based detailed supply chain info, adjustments of privacy laws and frameworks.
Agreement-based HR replacement procedures.
Agreement-based live-cam and enhanced monitoring.
Engineering cyber tools as an addition to the network and digital-based cyber security tools.
